Authored by Patrick Ciavolella, Head, Malware Desk and Analytics, The Media Trust
Mobile Redirects Targeting iOS Devices.

In the digital marketing and media world, the user experience is king. HTML5 has played a key role in enabling developers to deliver a richer yet smoother user experience and, as everyone presumed, without the security risks frequently associated with plugins like Flash. In fact, over the past five years, developers, along with publishers and browser providers, have staged a mass exodus from Flash technology into HTML5, which seemed to promise greater security and more advanced web app features. In 2015, when the Interactive Advertising Bureau updated its digital advertising guide with best practices for using HTML5, they cited security as the chief reason behind publishers’ adoption of HTML5.
Over the past two months, The Media Trust malware team has discovered numerous malware incidents which call into question HTML5’s mantle of security. The malware, which has produced at least 21 separate incidents affecting dozens of globally recognized digital media publishers and at least 15 ad networks, uses JavaScript commands in order to hide within HTML5 creative and avoid detection. The scale of the infection marks a turning point for HTML5’s presumed security and demonstrates the advances malware developers have made in exploiting the open standards’ basic functionality to launch their attack.
HTML5’s Cloak and Dagger
HTML5 renders multimedia content—images, videos, audio—and runs on any computer and mobile device. The very same attributes that enable it to render popular formats without external plugins also can be used to break apart malware into chunks, making it hard to detect, and reassemble those pieces when certain conditions are met. The malware incidents recently identified by The Media Trust carried out their attacks by infecting HTML5 ads.
The screenshot below illustrates the malware’s behavior through the call chain. When a user views the media publication’s webpage, the JavaScript checks the device for key criteria, namely (1) whether the device is iOS and (2) whether the user is connected via their carrier. When the device meets these criteria, the JavaScript inserts the malicious code into the website (see line 20). The malware is reassembled and issues a separate call which automatically redirects to a new domain that serves a pop-up soliciting input of personal information. Meanwhile, the JavaScript puts together the ad’s various components (see lines 48 through 56).
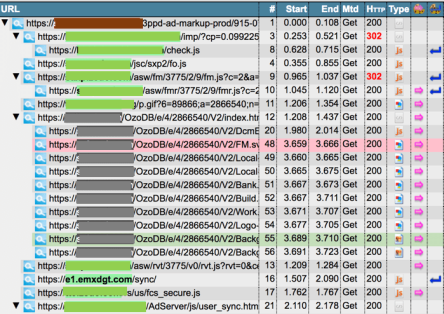
Figure 1: Call Chain of 2018 HTML Malware Phishing Via an Ad
HTML5 malware are by no means new. In 2015, just as the retreat from Flash began in earnest, researchers discovered several techniques to convert HTML5 into a safe haven for malware. Their techniques used APIs, which in turn employed the same obfuscation-deobfuscation JavaScript commands in delivering drive-by malware. In 2016, tech support scammers used an HTML5 bug to freeze computers and obtain unsuspecting users’ phone numbers. One year later, The Media Trust identified a small number of HTML5 malware delivered pell-mell through a few online publishers. This year’s incidents are different because they require no interaction with the victim and are targeting devices known to make detecting malware even more challenging.
It is important to note that throughout the years, no version of the HTML5 malware has been stopped by antivirus solutions.
HTML5 Malware in the GDPR Era
In this instance, the HTML5 malware was designed to entice victims to enter their information in response to a pop-up ad and is quickly coursing through the digital marketing and media world, waiting for individuals with the right devices to trigger the collection of personally identifiable information. Thwarting this malware will be more urgent than ever as the European General Data Protection Regulation (GDPR) is applied to organizations around the world—regardless of where they are located–that collect personal information on EU citizens. The GDPR, which is poised to penalize infringing organizations as much as four percent of their annual revenues, is merely a precursor to what appears to be a growing trend around the world towards greater online privacy. Public weariness with hacking and with platform providers sharing user data with their partners has spiked distrust even in brands whose reliability and transparency were previously believed to be unassailable.
What steps should organizations take? First, they should continuously scan in real-time their digital assets for vendors and code. Second, organizations should share and clearly written policies and enforce privacy clauses with their vendors as part of creating a compliance culture within their digital ecosystem. GDPR can impose penalties on an organization and their data processing partner even if the partner is entirely at fault. Third, they need to lay out an expeditious process that details how they will respond to a breach or to any unauthorized vendor activity. That process should include the immediate termination of any vendor that continues to break policy or clauses after being put on notice. Finally, companies should have quick access to information in case they are required to respond to a regulatory review.